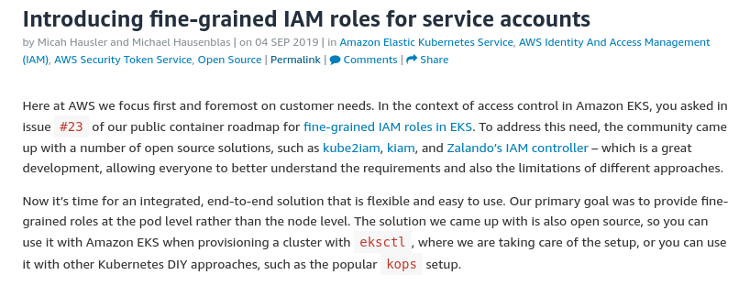
K8s OIDC Endpoint
Jason Smith

https://www.linkedin.com/in/jason-richard-smith
https://github.com/jasonrichardsmith
https://twitter.com/jasonrichardsmi
Follow Along
kubesec.jasonrichardsmith.org
Intercluster Control?
Who is doing this?
How are you doing it?
Controlling one cluster from the pod in another
Want to do this?
CI/CD?
OIDC Discovery - KEP
https://github.com/kubernetes/enhancements/blob/master/keps/sig-auth/20190730-oidc-discovery.md
This Kubernetes Enhancement Proposal covers the purpose of adding OIDC discovery in Kubernetes
What I will be discussing today.
KEP
Goals
- Allow (authorized) systems to discover the information they need to authenticate KSA tokens.
- Attempt compatibility with OIDC: common libraries that authenticate OIDC tokens should be able to authenticate KSA tokens.
- Support authentication when the API server is not directly reachable by the relying party.
https://github.com/kubernetes/enhancements/blob/master/keps/sig-auth/20190730-oidc-discovery.md
Micah Hausler and Michael Hausenblas
EKS and IAM introduced last year
Introduced the same functionality
IAM accepts oidc identities
Self Hosted OIDC
 https://github.com/aws/amazon-eks-pod-identity-webhook/blob/master/SELF_HOSTED_SETUP.md
https://github.com/aws/amazon-eks-pod-identity-webhook/blob/master/SELF_HOSTED_SETUP.md
A guide how to run your own discovery endpoints
BUT This is static
The Components
- OIDC Discovery Document
- Projected Service Accounts
- Client
1: OIDC Discovery Document
.well-known/openid-configuration
{ "jwks_uri": "https://cluster.example.com/openid/v1/jwks", "response_types_supported": [ "id_token" ], "subject_types_supported": [ "public" ], "id_token_signing_alg_values_supported": [ "RS256", "ES256" ],}1: OIDC Discovery Document
/openid/v1/jwks
{ "keys": [ { "kty": "RSA", "alg": "RS256", "use": "sig", "kid": "ccab4acb107920dc284c96c6205b313270672039", "n": "wWGfvdCEjJJy...", "e": "AQAB" } ]}https://openid.net/specs/openid-connect-discovery-1_0.html
The JSON Web Key Set (JWKS) is a set of keys which contains the public keys used to verify any JSON Web Token (JWT) issued by the authorization server and signed using the RS256 signing algorithm.
2: Projected Service Accounts
apiVersion: v1kind: Podmetadata: name: a-podspec: containers: - name: a-container image: container volumeMounts: - mountPath: "/var/run/secrets/myfolder/" name: psa-token volumes: - name: psa-token projected: sources: - serviceAccountToken: audience: "my.audience.here" expirationSeconds: 86400 path: tokenhttps://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/#service-account-token-volume-projection
2. Projected Service Accounts
vs Service Accounts
"You can specify desired properties of the token, such as the audience and the validity duration. These properties are not configurable on the default service account token."
3. The Client...
The Process
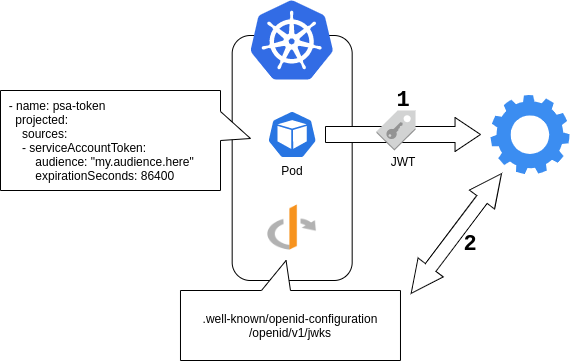
K8s - OIDC Provider
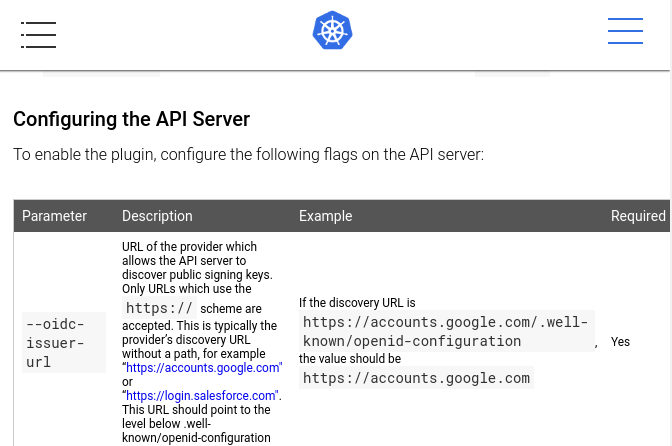 https://kubernetes.io/docs/reference/access-authn-authz/authentication/#configuring-the-api-server
https://kubernetes.io/docs/reference/access-authn-authz/authentication/#configuring-the-api-server
The Process - With K8s
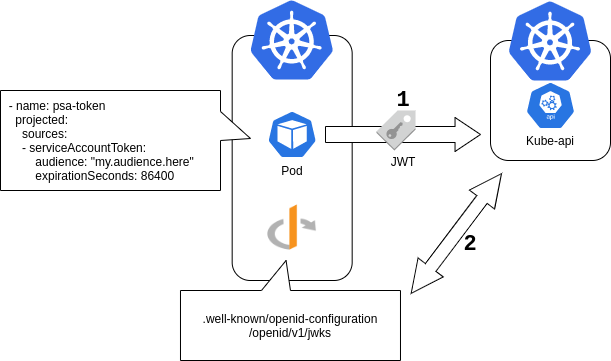
Clients
- AWS
- Kubernetes
Clients
"We aren't trying to make the KSA token process fully compliant with OIDC specifications."
https://github.com/kubernetes/enhancements/blob/master/keps/sig-auth/20190730-oidc-discovery.md
Clients
- AWS
- Kubernetes
Control Patterns
Control Patterns
?